This is an old revision of the document!
Table of Contents
Network Security Assesment
NOTE : Some link might not work, but search based on the name and site.
technical results to management categories
OS configuration
Vulnerabilities due to improperly configured operating system software
Software maintenance
Vulnerabilities due to failure to apply patches to known vulnerabilities
Password/access control
Failure to comply with password policy and improper access control settings
Malicious software
Existence of malicious software (Trojans, worms, etc.) or evidence of use
Dangerous services
Existence of vulnerable or easily exploited services or processes
Application configuration
Vulnerabilities due to improperly configured applications
Recognized Assesment Standard
PCI Data Security Standards
Other Assessment Standards and Associations
Investigation of Vulnerabilities
commercial feed services
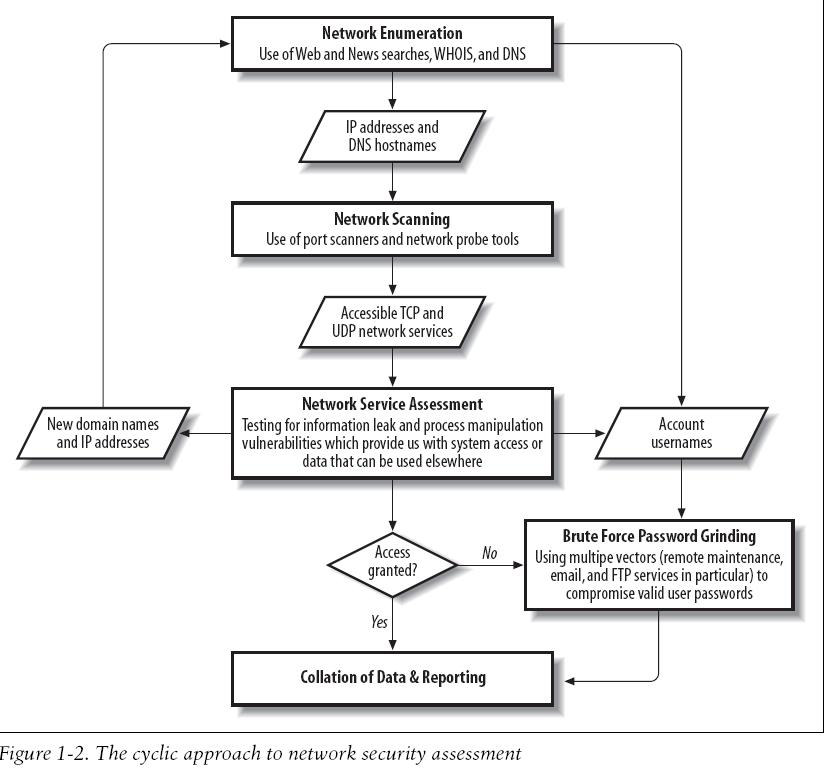
Cyclic Assesment Process
Reconnaissance Tools
Free Network Scanning Tools
Commercial Network Scanning Tools
Exploitation Frameworks
Commercial Exploitation Frameworks
Web Application Testing Tools
Active open source web application crawling and fuzzing tools
Commercial Web Application Scanning Tools
Protocol Dependent Assesment Tools
Enumeration and Information gathering tools
Brute-force password guessing tools
DNS
- nslookup
- host and dig
- ghba (available at tools links it is source)
BGP Querying
- We can cross-reference AS11278 at http://fixedorbit.com/search.htm to reveal the IP blocks associated with the AS number.
- Many BGP looking glass sites and route servers can be queried to reveal this information. Route servers are maintained by ISPs and can be connected to using Telnet to issue specific BGP queries. A list of looking glass sites and route servers is maintained by NANOG at http://www.nanog.org/lookingglass.html
HTTP and HTTPS
Using google
Enumerating CIA contact details with googl
+"ucia.go" +tel +fax
Effective search query strings
allintitle: "index of /" site:.redhat.com
** Another site for effective search Netcraft
How to use whois effectively
* whois cs-security-mnt * whois "@citicorp.com" @whois.arin.net
Forwarding DNS query
- Forward DNS querying transfer using nslookup
#nslookup >set querytype=any >cia.gov >server auth100.ns.uu.net #zone transfer using nslookup. >ls -d ucia.gov
- Using dig to perform a DNS zone transfer
dig @relay2.ucia.gov ucia.gov axfr
- PTR record enumeration through DNS zone transfer
dig @relay2.ucia.gov 129.81.198.in-addr.arpa axfr
Forward DNS Grinding
- Using a forward DNS lookup to enumerate MX records
$ nslookup > set querytype=mx > bankofengland.co.uk
- Windows tool that support dictionary-based hostname grinding
txdns -f mail-dict.txt bankofengland.co.uk
Reverse DNS Sweeping
$ghba 198.81.129.0
Web Server Crawling
Automating Enumeration
SMTP Probing
Reading/Understanding Header of Returned Mail.
The original message was received at Fri, 1 Mar 2002 07:42:48 -0500 from ain-relay2.net.ucia.gov [192.168.64.3] ----- The following addresses had permanent fatal errors ----- <blahblah@ucia.gov> ----- Transcript of session follows ----- ... while talking to mailhub.ucia.gov: >>> RCPT To:<blahblah@ucia.gov> <<< 550 5.1.1 <blahblah@ucia.gov>... User unknown 550 <blahblah@ucia.gov>... User unknown ----- Original message follows ----- Return-Path: <hacker@hotmail.com> Received: from relay2.net.ucia.gov by puff.ucia.gov (8.8.8+Sun/ucia internal v1.35) with SMTP id HAA29202; Fri, 1 Mar 2002 07:42:48 -0500 (EST) Received: by relay2.net.ucia.gov; Fri, 1 Mar 2002 07:39:18 Received: from 212.84.12.106 by relay2.net.ucia.gov via smap (4.1) id xma026449; Fri, 1 Mar 02 07:38:55 -0500
Reading above header in English
In particular, the following data in this transcript is useful:
• The Internet-based relay2.ucia.gov gateway has an internal IP address of
192.168.64.3 and an internal DNS name of relay2.net.ucia.gov.
• relay2.ucia.gov is running TIS Gauntlet 4.1 (smap 4.1, a component of TIS
Gauntlet, is mentioned in the via field).
• puff.ucia.gov is an internal SMTP mail relay system running Sun Sendmail
8.8.8.
• mailhub.ucia.gov is another internal mail relay running Sendmail (this can be
seen from analyzing the SMTP server responses to the RCPT TO: command).
IP Network Scanning
ICMP Probing
From a network scanning perspective, the following types of ICMP messages are useful:
- Type 8 (echo request)
- Type 13 (timestamp request)
- Type 15 (information request)
- Type 17 (subnet address mask request)
ICMP Probing Tools
- SING - Send ICMP Nasty Garbage (is a command-line utility that sends customizable ICMP probes.)
$ sing -echo 192.168.0.255 $ sing -tstamp 192.168.0.50 $ sing -mask 192.168.0.25
- Nmap - can perform ICMP ping sweep scans of target IP blocks easily
$ nmap -sP -PI 192.168.0.0/24 (Performing a ping sweep with Nmap)
- ICMPScan - ICMPScan is a bulk scanner that sends type 8, 13, 15, and 17 ICMP messages
You can get how to use by simply running application $ icmpscan –c -t 500 -r 1 192.168.1.0/24
Enumerating subnet network and broadcast addresses with Nmap
nmap -sP 154.14.224.0/26
Useful details about subnet network and broadcast addresses and CIDR slash notation can be found at http://en.wikipedia.org/wiki/ Classless_Inter-Domain_Routing.
TCP Port Scanning
Accessible TCP ports can be identified by port scanning target IP addresses. The
following nine different types of TCP port scanning are used in the wild by both
attackers and security consultants:
Standard scanning methods Vanilla connect( ) scanning Half-open SYN flag scanning Stealth TCP scanning methods Inverse TCP flag scanning ACK flag probe scanning TCP fragmentation scanning Third-party and spoofed TCP scanning methods FTP bounce scanning Proxy bounce scanning Sniffer-based spoofed scanning IP ID header scanning
Using Nmap to perform IP ID header scanning
nmap -P0 -sI 192.168.0.155 192.168.0.50
Fragmenting Probe Packets
Probe packets can be fragmented easily with fragroute to fragment all probe packets
flowing from your host or network or with a port scanner that supports simple
fragmentation, such as Nmap. Many IDS sensors can’t process large volumes of fragmented
packets because doing so creates a large overhead in terms of memory and
CPU consumption at the network sensor level.
Fragtest
Dug Song’s fragtest utility can determine exactly which types of fragmented
ICMP messages are processed and responded to by the remote host. ICMP
echo request messages are used by fragtest for simplicity and allow for easy analysis;
the downside is that the tool can’t assess hosts that don’t respond to ICMP
messages.
After undertaking ICMP probing exercises (such as ping sweeping and hands-on use
of the sing utility) to ensure that ICMP messages are processed and responded to by
the remote host, fragtest can perform three particularly useful tests:
• Send an ICMP echo request message in 8-byte fragments (using the frag option)
• Send an ICMP echo request message in 8-byte fragments, along with a 16-byte
overlapping fragment, favoring newer data in reassembly (using the frag-new
option)
• Send an ICMP echo request message in 8-byte fragments, along with a 16-byte
overlapping fragment, favoring older data in reassembly (using the frag-old
option)
Here is an example that uses fragtest to assess responses to fragmented ICMP echo
request messages with the frag, frag-new, and frag-old options:
$ fragtest frag frag-new frag-old www.bbc.co.uk
frag: 467.695 ms
frag-new: 516.327 ms
frag-old: 471.260 ms